Scope:
This post will guide you to setting up the Web Application Firewall to present the UniFi controller to the Internet with a reverse proxy & SSL certificate.
Prerequisites:
- A fully qualified domain namd (FQDN) for the UniFi controller (eg: unifi.domain.tld)
- Public hosted DNS record for the above FQDN pointing to the public IP address terminated at the Sophos SG/UTM
- A static public IP address terminated at the Sophos SG/UTM
- SSL Certificate(s) matching the FQDN(s) installed on the Sophos (see Let’s Encrypt if you want to use this feature)
- Internal UniFi controller you wish to make externally accessible via the WAF
Setup Internal Server:
Login to the SG UTM
Head to Webserver Protection > Web Application Firewall in the side menu
Click on the Real Webservers tab
Click the New Real Webserver… button
- Enter the name to be the same as the Internal UniFi controller host, add an underscore followed by the port number. Example: UNIFI_8080
- In the host picker, add the host. If the host item doesn’t actually exist in the Sophos, click the + icon to create a new internal host entry
- The type options are HTTP and HTTPS. Use HTTP for ports 8080, 8880, and use HTTPS for 8443, 8843, etc.
- Set the port to match what you entered after the underscore in the Name field
- Click Save
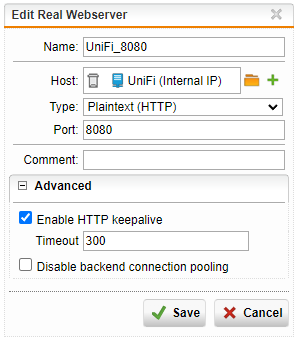
Repeat for the rest of the entries for the UniFi controller so you have an entry for each of the four required services ports
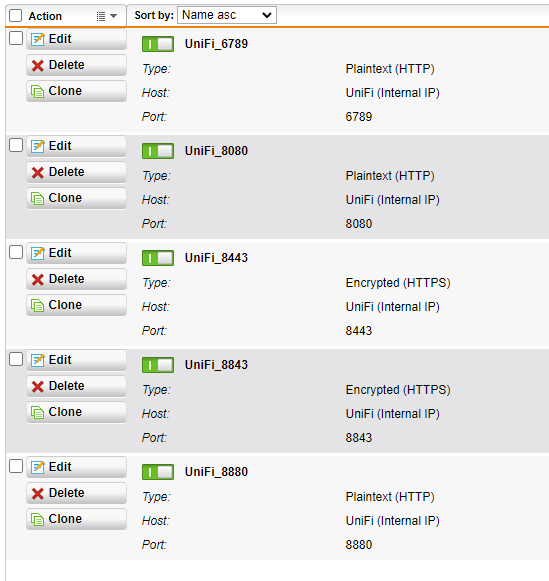
Now head to the Virtual Webservers tab
Click the New Virtual Webserver… button
- Enter the name as the public FQDN followed by an underscore and the port number – makes for ease of identification
- Select the WAN interface the FQDN resolves to via public DNS
- Set the appropriate type (HTTP, HTTPS, or HTTPS & redirect) – see below for these
- Set the port to match the port you specified in the name (warning, when you change the above type, the port reset to the default (80 or 443)
- Enter in the FQDN in the domains list
- Place a tick next to the appropriate matching Real webserver with the matching port located inthe Real Webservers for path ‘/’ list
- For the firewall profile, right now we won’t select anything – this can be adjusted at a later stage if / when required.
- Don’t change the theme
- Expand out the Advanced section and ensure all three selections items are deselected as these are not used for UniFi controllers.
- Click save and repeat for each required virtual server.
Note, when adding in virtual webserver with the type set to either HTTPS or HTTPS & redirect, the Certificate dropdown list becomes available – this is where you will select the appropriate SSL certificate with the matching FQDN (or wildcard certificate).
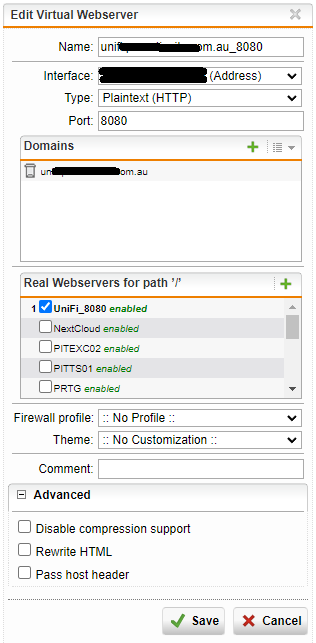
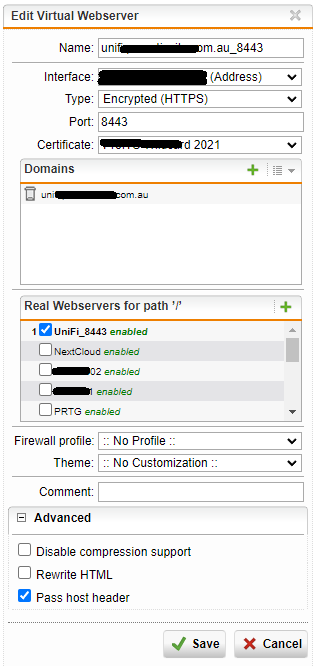
Once they have been added, the virtual servers will look like this:
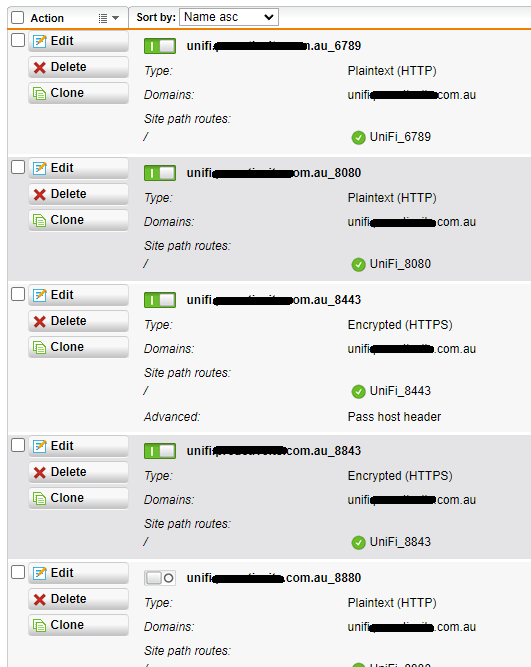
Note:
- Ports 6789, 8080 and 8880 need to be set to HTTP
- Ports 8443 and 8843 need to be set to HTTPS
Now we need to enable WebSocket passthrough for the 8443 entry otherwise the controller will contantly complain that WebSockets aren’t working
Click on the Site Path Routing tab
Locate the site path routing entry automatically created for the 8443 entry and click Edit
Expand out the Advanced box and place a tick next to the checkbox item labelled Enable WebSocket passthrough
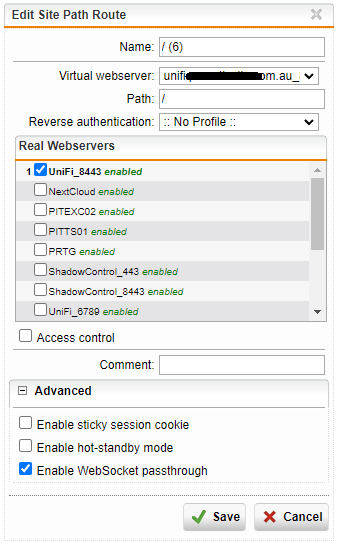
Ensure all the Real Servers and Virtual Servers are switched on
Next we need to check the Firewall NAT settings
Head over to Network Protection > NAT
Click on the NAT tab
Locate and turn off any NAT rules that may be present for the UniFi controller using the same ports as you configured in the Web Application Firewall (so ensure that these are OFF: 8080, 8443, 6789, 8843, and 8880)
Ensure a NAT rule exists and is enabled for STUN to passthrough to the controller.
Create a New NAT Rule…
- Rule type: DNAT
- For traffic from: Any
- Using service: STUN 3478 (you may need to create this rule, it will be a UDP port)
- Going to: the same public WAN interface you are using on the WAF for the UniFi controller
- Change the destination to: the internal UniFi controller host
- Tick to enable Automatic firewall rule
- Click save.
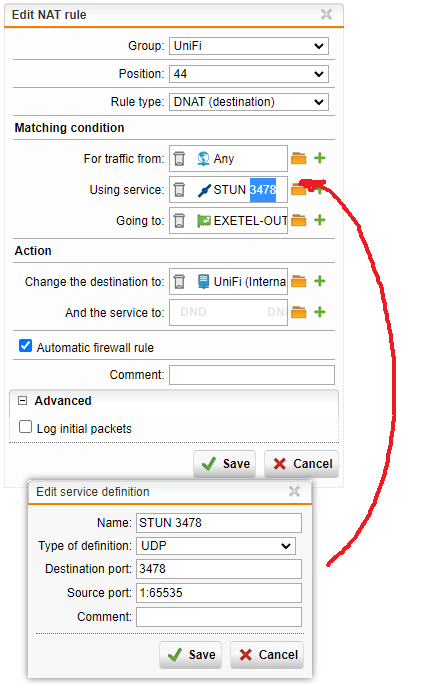
Switch on the new NAT rule to activate it.
Finally, we need to create an outbound firewall to allow the internal UniFi controller to access the network beyond the firewall
Head to Network Protection > Firewall
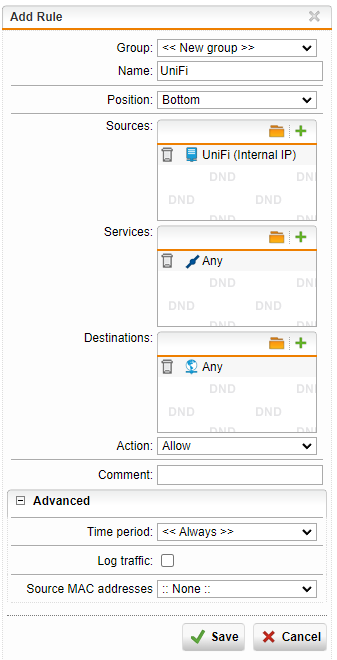
Click New Rule…
- Create a new Group called UniFi
- Source: select the internal UniFi host
- Service: Any
- Destinations: Any
- Action: Allow
- Save
- Enable the rule to activate it.
Now you should have a working UniFi controller that is publicly accessible (and internally accessible) that is behind the Sophos WAF and you an use the FQDN to access it with a valid SSL certificate.
Some Notes & WIP:
In the above examples, the virtual web server for 8880 is currently disabled and a NAT rule exists for 8880 instead, as this port is used for the UniFi controller’s guest WiFi web portal. I am in the middle of troubleshooting an issue where this wouldn’t work from behind the WAF. I will update this space once I have resolved this.