This guide is intended to demonstrate the key tasks to perform before adding a new Domain Controller to Active Directory, or, when performing extended maintenance on older AD environments where domain controllers have been added & removed in its lifetime.
Get a list of all Domain Controllers using an administrative level PowerShell session:
Get-ADDomainController -Filter * | ft Name,Hostname,OperatingSystem,IPv4Address
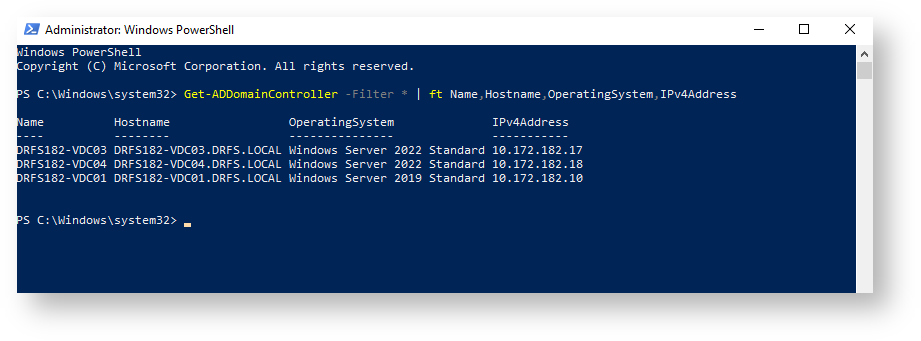
Confirm in Active Directory Users and Computers (ADUC) that this list corresponds with the Domain Controllers OU (typical in simple environments that they all live in the same OU)
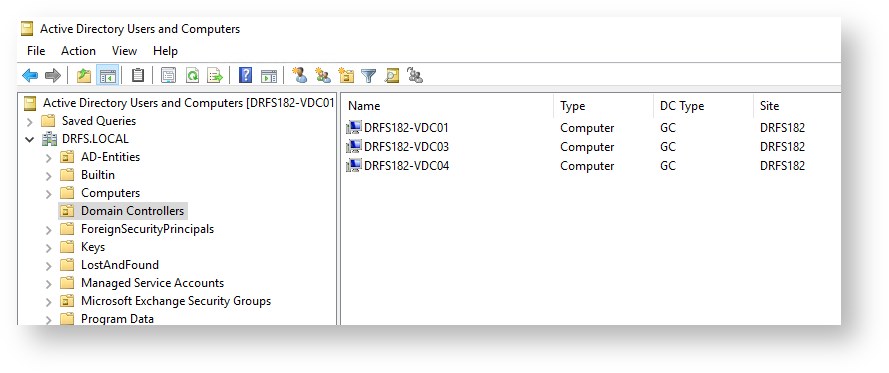
Note there are three domain controllers and they’re all Global Catalog located in the same site
Next, launch ADSI Edit
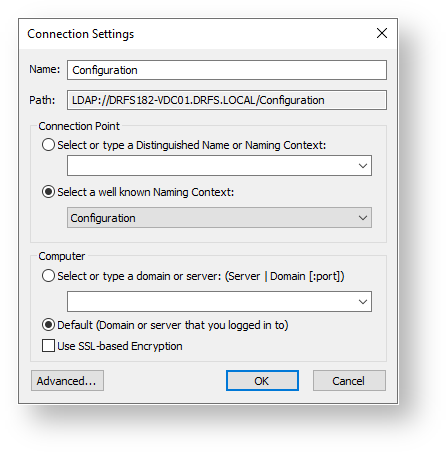
Right-click ADSI Edit in the top of the left tree, click Connect to…
Under the drop down list labelled “Select a well known Naming Context:” select Configuration
Click OK
Expand out:
Configuration > CN=Configuration > CN=Sites > CN=(site name) > CN=Servers
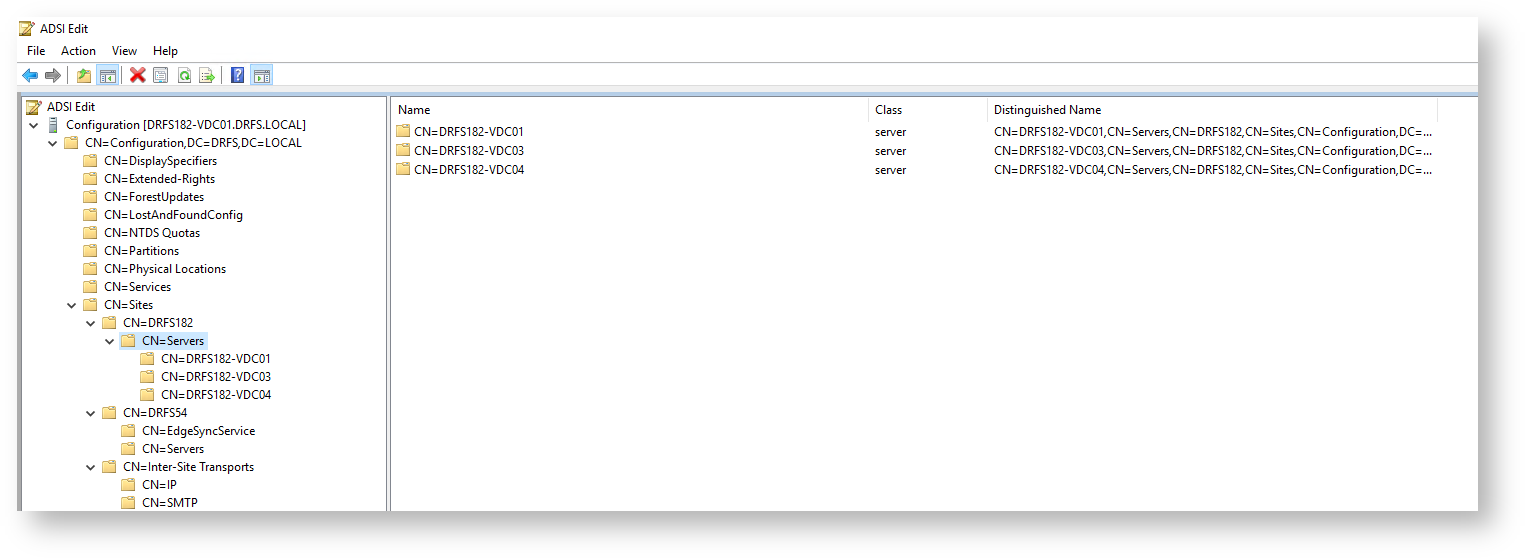
Confirm that this list matches that of what you got out of PowerShell earlier
Check each of the CN=Sites for all other CN=Servers – you’re confirming all sites for the presence of their DC (if they have them) or for any remnants of previous domain controllers still present in ADSI Configuration…
Example: This AD environment has multiple sites, and the site named DRFS54 no longer has any domain controllers, so after demoting them, a clean up was performed to ensure there are no remnants of them…
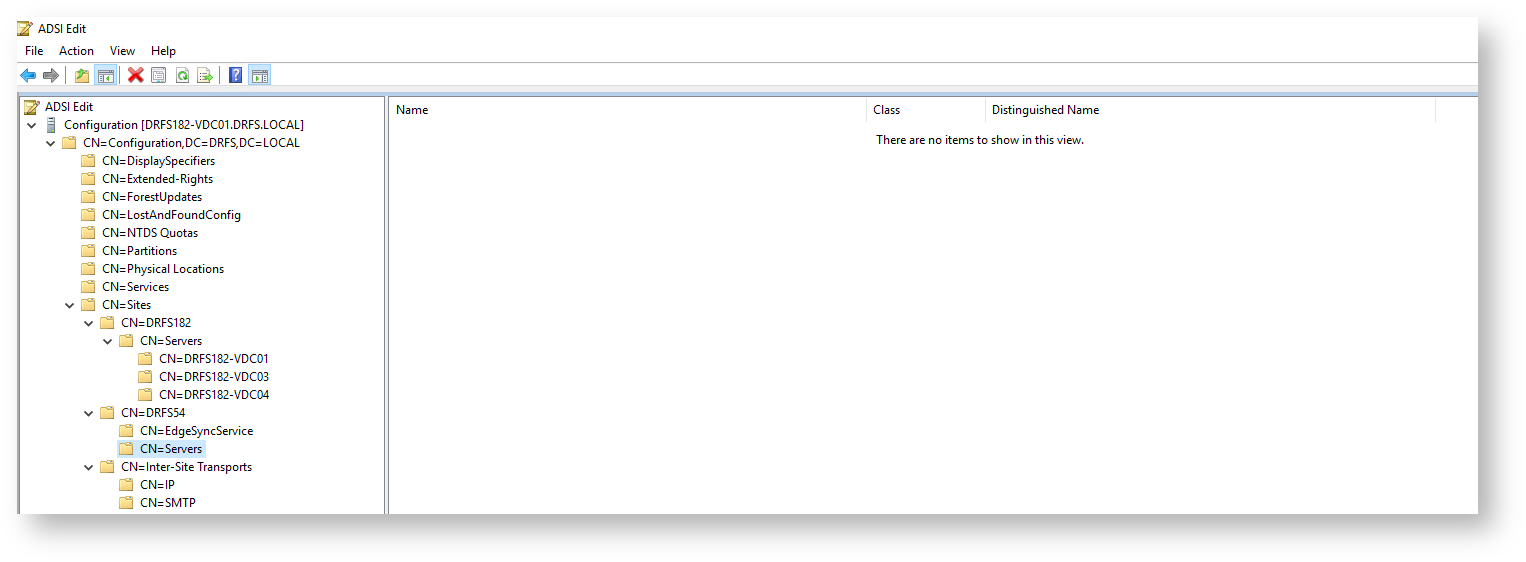
Next, launch the DNS Manager
You’ll need to expand out EVERY folder for both forward and reverse lookup zones on the left – you’re going to comb through EVERY one of these – checking for previous, no longer existent domain controllers listed, and ensuring that each zone has only current domain controllers listed…
So in the various AD-specific zones & meta data, check that no old DC’s remain – remove any old ones
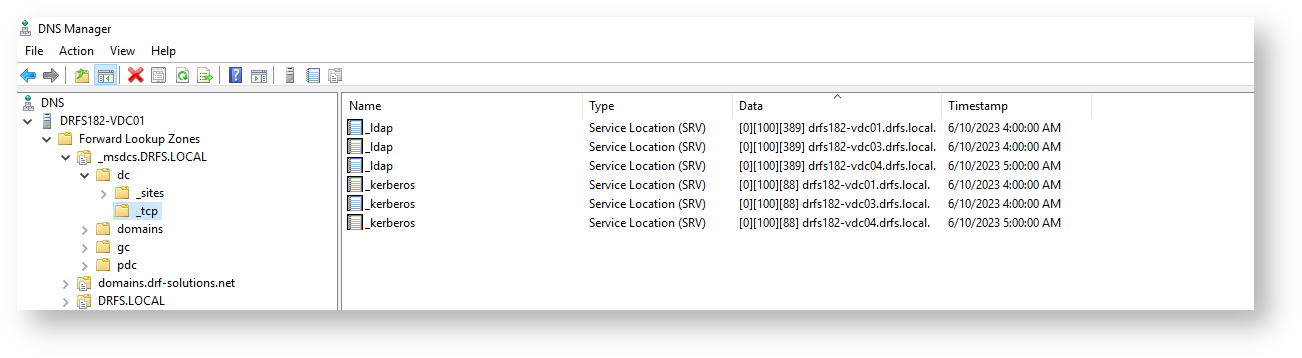
For each zone, right click and select Properties, then click the Name Servers tab
Check & confirm that only current servers are listed – remove any old ones
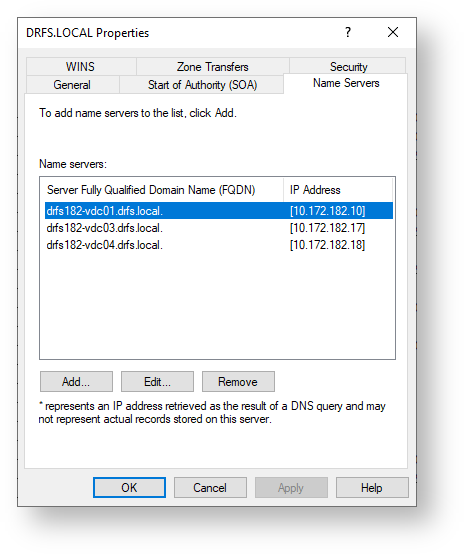
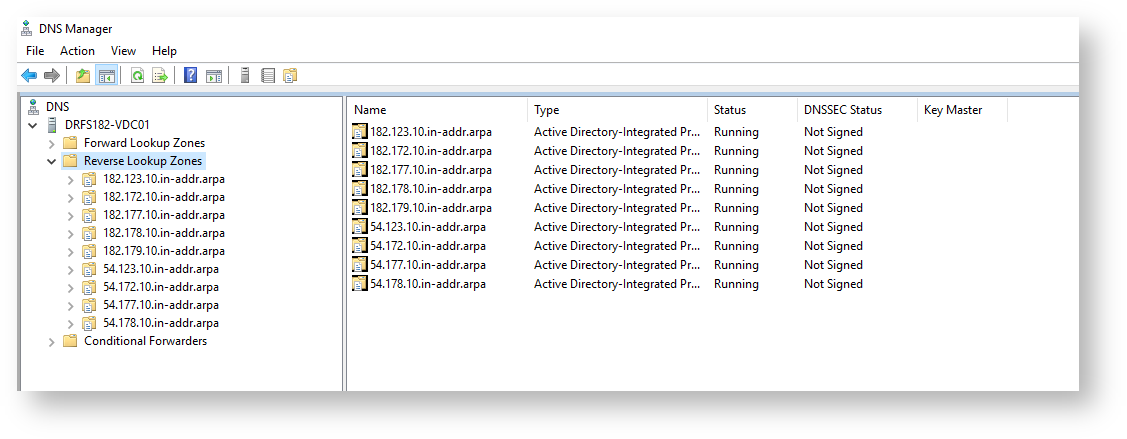
Repeat the same for all Reverse Lookup Zones. If there are none, it would be good to create any required reverse lookup zones – but do this after the full health check has been completed & errors fixed… A reverse lookup zone will be required for any LAN & VPN subnet that might contain other PCs & servers that will communicate with AD, so in the case where there are multiple sites and remote access, each site and the VPN subnets will be created here.
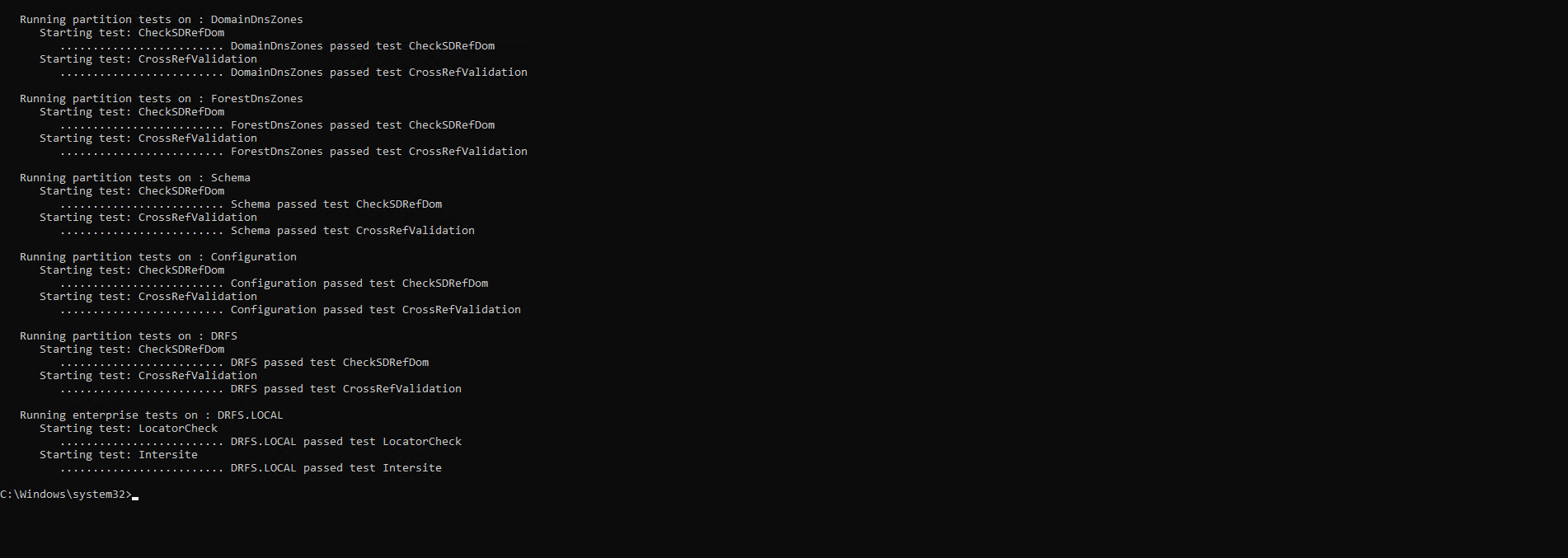
Next we’ll move onto DCDIAG
Using an elevated command prompt from one of the domain controllers, issue the command:
DCDIAG
Check the output for any errors
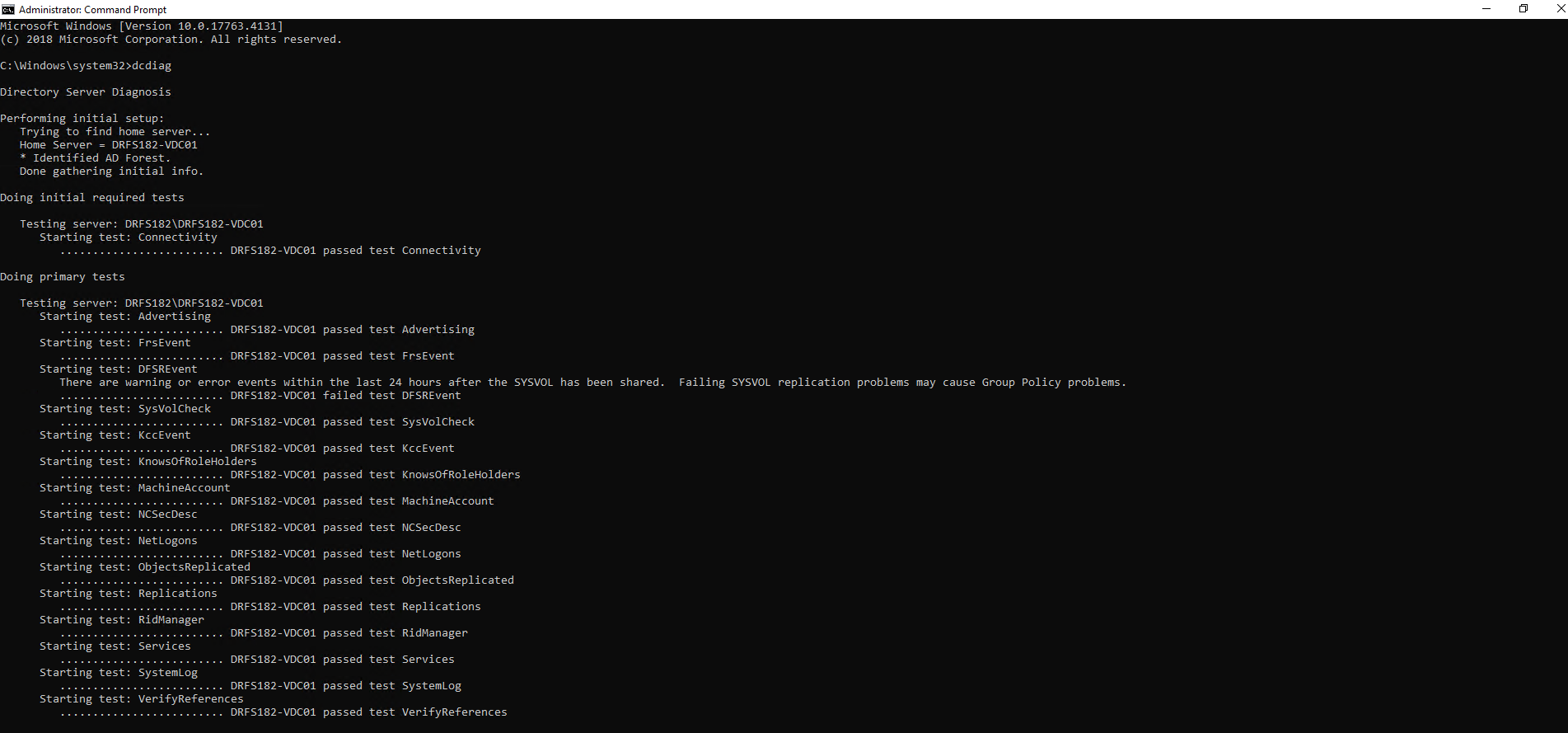
Repeat this on every domain controller
If the domain controller has a VSS-level backup job or has been rebooted in the last 24 hours, you may receive the following error:
Starting test: DFSREvent There are warning or error events within the last 24 hours after the SYSVOL has been shared. Failing SYSVOL replication problems may cause Group Policy problems.
![]()
This is normal and expected, as during either of the above mentioned scenarios, the DFSR service is stopped or paused, a VSS (volume snap shot) is taken, then the service is started again.
Check for other errors and fix up as best as you can – if you’ve had to perform a clean up, then you may need to wait up to 48 hours before some of the errors clear up and no longer show up in DCDIAG results. Google and ChatGPT are your friends here when it comes to errors.
Next, in an elevated command prompt, issue the command:
netdom query fsmo
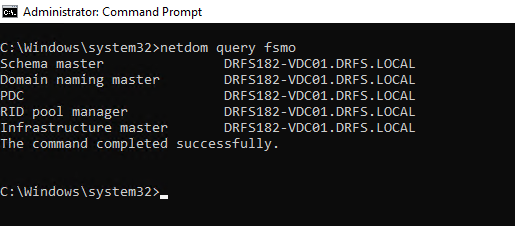
This will output what AD believes is the primary role holding domain controller. If the AD is relatively old, has had servers added & removed in its lifetime, then. perform this check on every domain controller to ensure congruency.
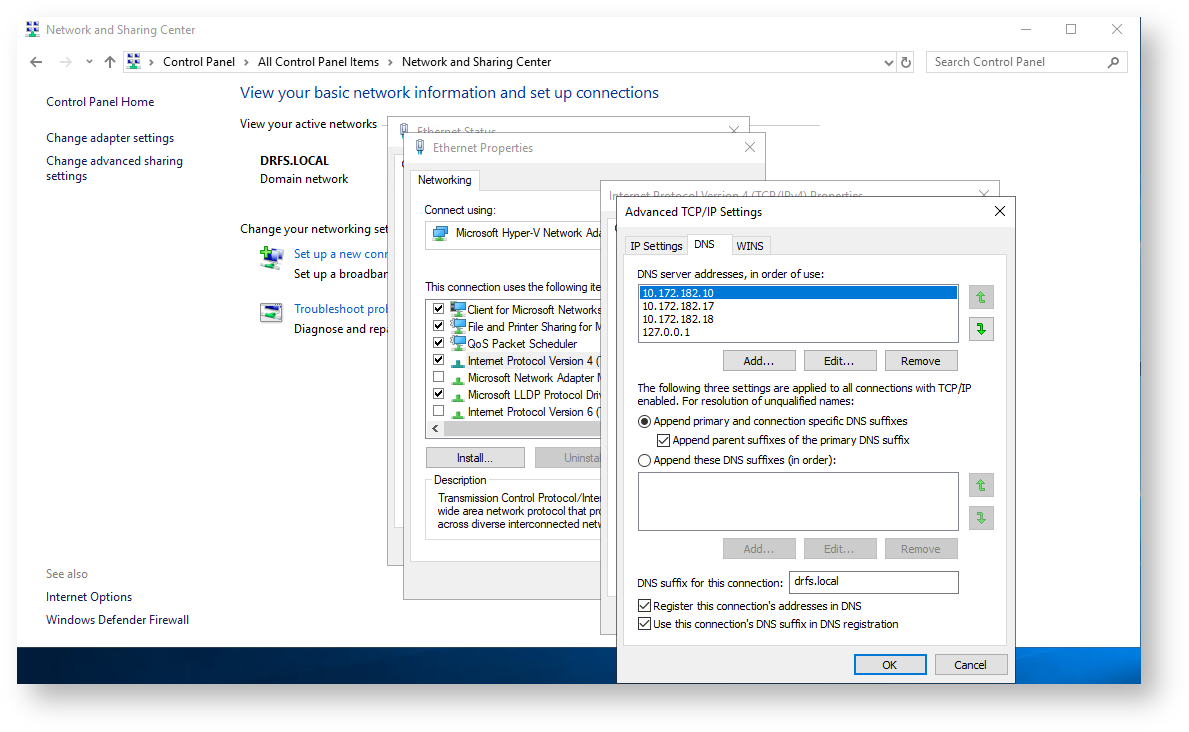
On every domain controller – edit the NIC DNS settings to ensure that every DC has each domain controller’s IP Address as a DNS server, ideally with the PDC/FSMO as the primary IP Address, then all other DCs, followed by its own IP address, fianlly followed up with 127.0.0.1 as the last DNS lookup IP address.
Ensure the AD domain name is in the DNS suffix with registration enabled.
After ensuring this is completed on every domain controller, wait up to 24 hours and perform a final DCDIAG on each domain controller. What you’re looking to achieve is a clean bill of health in DCDIAG as pictured in the above examples!
Now go back and add in the missing Reverse Lookup Zones in DNS manager – check this has replicated across to each DC.
Note: The example AD environment above is for illustration purposes only, may not be reflective of the environment you’re attempting to follow this guide in, and is a testing lab only.